Device Fingerprinting :Enhance Security With IP & Device Analysis
Enable your business to swiftly identify fraud patterns, detect malware, and combat bots while enhancing customer protection.
- Setup in Minutes
- No Credit Card
- Cancel Anytime
High-Risk Customers
Device fingerprinting: Identify suspicious
users by detecting harmful IP's
IP & Device Intelligence Lookup provides insights into user connections, enhances risk assessments, evaluates VPN/Tor users, and aids KYC, AML processes, and chargeback prevention.
Identify Suspicious IP's and VPN's
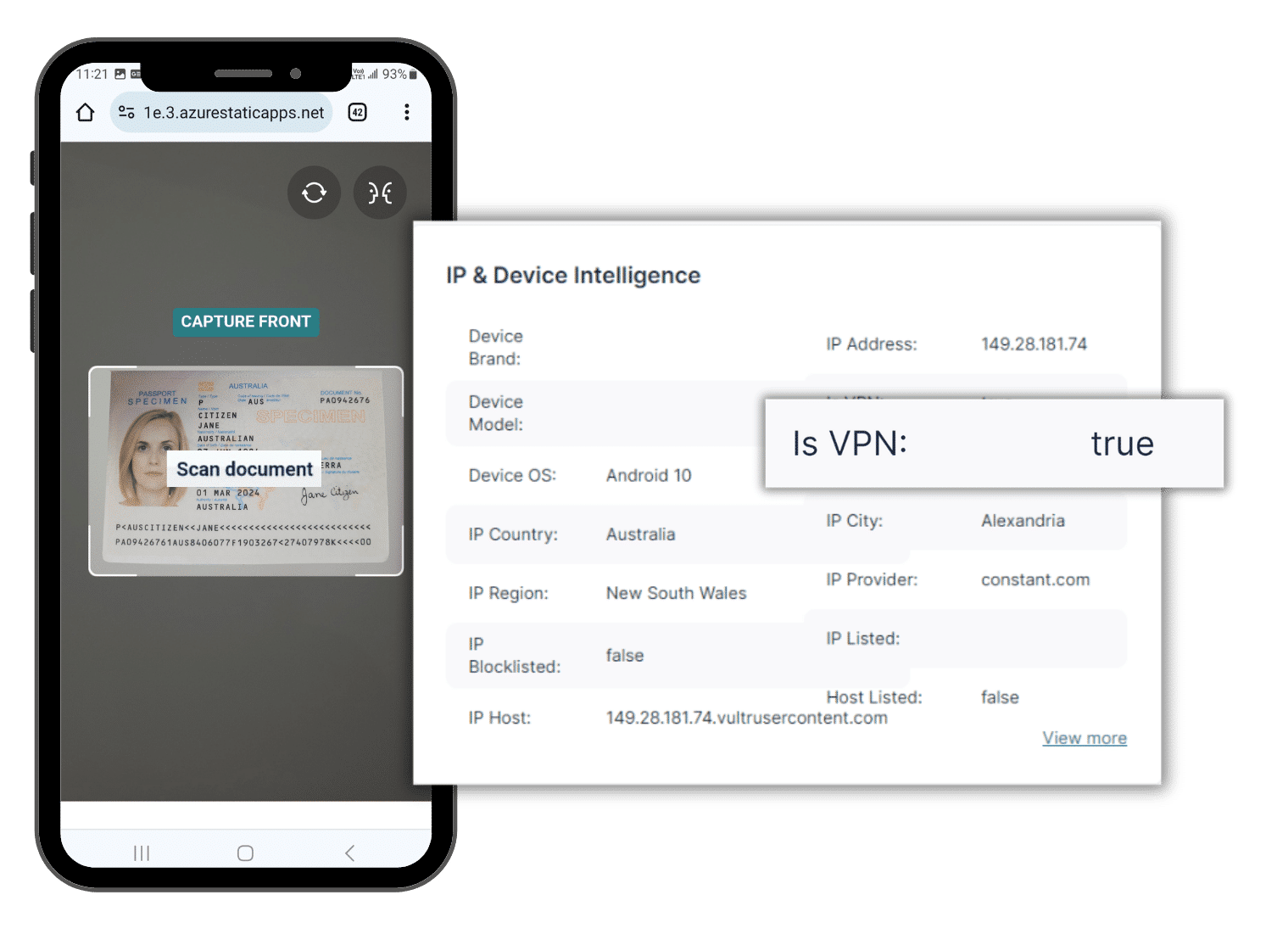
Retrieve valuable IP address information with device fingerprinting
Identify an IP address's geolocation down to the city level, including geographic coordinates and local details. Our database updates in real time as internet address allocations change and new IP ranges become available.
IP Probe
Device fingerprinting: Analyze and extract provider information for a single IP
IP probe performs real-time network-level checks on given IPs. We determine the provider type and detect VPN or proxy software. This helps identify potential bots and fraudulent applicants.
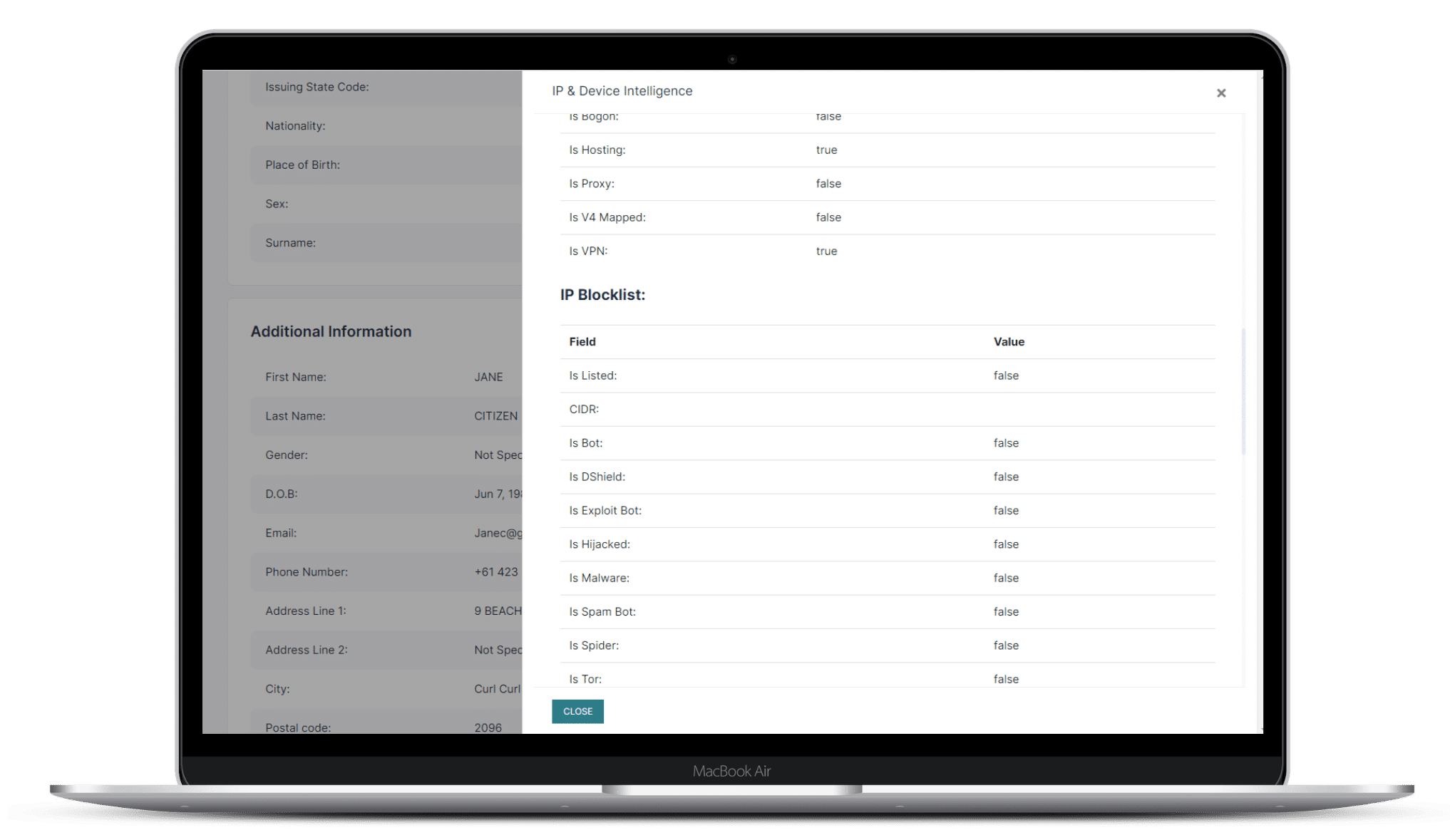
Identify Dangerous IP's
Device Fingerprinting for Malicious IP detection
ScreenlyyID's device fingerprinting will run an IP blocklist check to identify malicious hosts, anonymous proxies, tor, botnets, spammers and more.
Block, filter or flag traffic to help reduce attacks on your networks and software stacks.
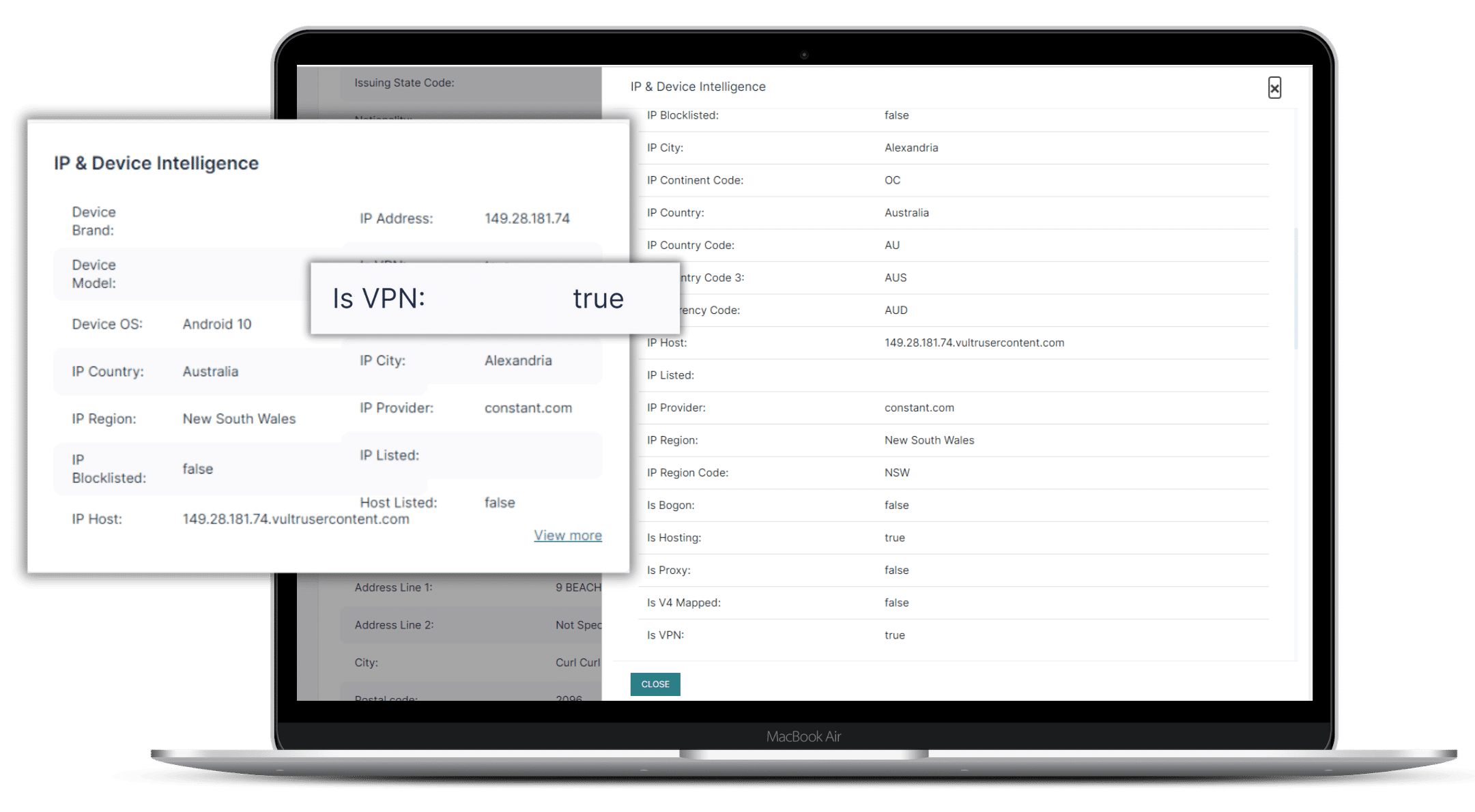
Comprehensive Risk Assessment
Device fingerprinting utilizing IP & device intelligence, strengthens risk assessments and enhances KYC models.
- Enhanced Risk Insights
- Informed KYC Models
- Accurate User Identification
- Comprehensive Data Analysis
What We Look For
Device fingerprintingwill identify suspicious proxies and VPN's
Geolocate IPs to city level, including coordinates and locale details. Our database updates in real-time with IP allocation changes. IP blocklist detects main categories of addresses.
Device fingerprinting will detect the following:
Lookup API to:
- Open Proxies
- Tor Nodes
- Public VPN's
- Spam hosts
- Phishing Hosts
- Malware Servers
- Attack Sources
- Criminal Netblocks
- Malicious Spiders
- Bots and Botnets
- Exploit Scanners
- Brute-Force Crackers
Host Reputation
Identify high risk device IDs with device fingerprinting
ScreenlyyID will check the reputation of an IP address, domain name or URL against a comprehensive list of blacklists and blocklists to discern high risk device IDs.
Under the hood there are three core blocklist components:
Assess New Users' Risk
Device fingerprinting: combat fraudulent users on a large scale

Real-Time Identity Checks
Device fingerprinting: Instantly validate new identities identities
Ensure verification with certainty. Use real-time digital identity and behavioral indicators to identify synthetic identities, enhance KYC and verify with confidence.

Stop Promo Abuse
Digital fingerprinting: prevent misuse

Eliminate Fraud
The ScreenlyyID fraud management
and preventions solution
ScreenlyyID email validation will help your organization eliminate all fraud related threats.
End-to-End Fraud Management & Customer Verification
Combine with other ScreenlyyID solutions for full identity verification and anti-fraud protection.
Experience real-time analytics, seamless data integration, in-depth customer journey analysis, and powerful marketing tools.
Digital Identity Verification
effectively verify new customers in seconds, safeguarding your business from identity fraud
eIDV Checks
Verify personal identity information against over 300+ independent and reliable data sources.
AML Screening
Use the extracted document data to run a full sanctions, PEP & global watchlist check on the individual.
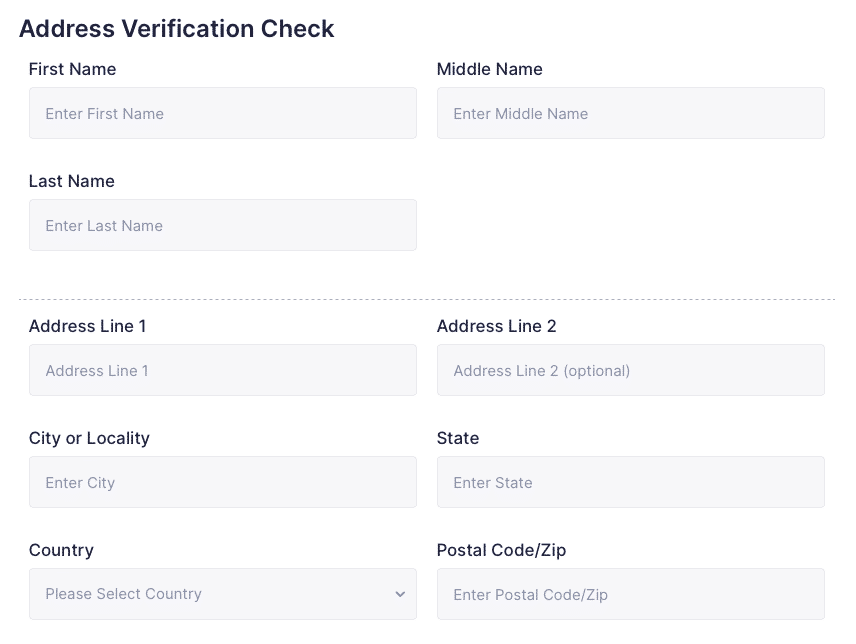
Address Validations
Validate and verify address’s in over 245 countries & territories. Simplify customer on-boarding, improve conversions.
Phone Validation
Define each stage of work to see what’s important and where things are getting stuck.
Email Validation
Validate Email Addresses in real time Reduce fraud and verify real users.
Customized Verification Solutions
No-Code, Bulk CSV, API, or live lookup, we’ve got you covered
ScreenlyyID's dashboard and API suite offers flexible integration options. You can conduct bulk verifications via CSV in the dashboard, integrate the API into your own systems, or send a no-code UI form to prospects for easy completion.
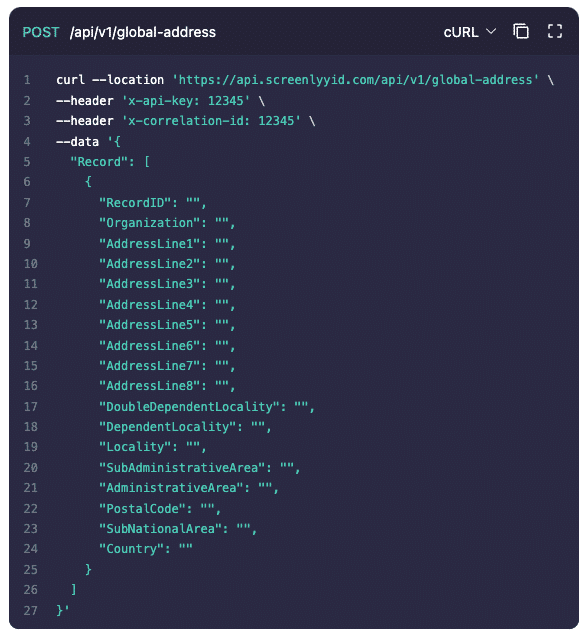
More Features
Unleash advanced KYC verification capabilities
Experience real-time analytics, no code integrations, advanced risk assessment, and powerful APIs to manage your organizations KYC Verification.
Frequently Asked Questions
We're here to answer all your device fingerprinting questions
Everything you need to know about ScreenlyyID's email validation solution. Can’t find the answer you’re looking for? Please chat to our friendly team.
Scree nlyyID's, device fingerprintinguses advanced algorithms to analyze IP addresses and device data, providing insights into user location, behavior, and potential risks. It works by cross-referencing data points against extensive databases in real-time.
ScreenlyyID's device fingerprinting API gathers data about the user's device, including browser type, operating system, and other identifiers. This information helps create a unique fingerprint, making it easier to spot suspicious patterns or repeated fraud attempts.
Yes, we offer flexible API integration options that allow our services to be seamlessly incorporated into your existing workflows, risk assessment systems, or customer onboarding processes.
Contact Us
Talk to an expert
Let's connect to discuss the possibilities and find the perfect solution for your business needs.
Complete the form, and one of our experts will reach out to you. You'll discover how our solutions can tackle your specific challenges, optimize your operations, and drive your growth.
- Explore industry-specific use cases
- Identify the best solution for you
- Get enterprise pricing
- Book a demo
Lets Connect....
Start Today
Start Verifying Customers Today
See how easily ScreenlyyID integrates verification into your onboarding process.
- Free Forever
- No Set Up Fees
- No Licencing Fees
- No Hosting Fees