- Home
- Remote Identity Verification
- eIDV – Electronic Identity Verification
eIDV - Electronic Identity Verification
ScreenlyyID provides a single access point to 70+ data partners and 300+ eIDV data sources around the world
- Setup in Minutes
- No Credit Card
- Cancel Anytime
Comprehensive Customer Insights
eIDV - Electronic identity verification
via one API
Rapidly verify and onboard customers at scale, regardless of an individual or business’s country of origin using our eIDV product.
Simplified eIDV Process
Scale customer onboarding with eIDV - electronic identity verification
ScreenlyyID enables instant eIDV - electronic identity verification, checking names, birth dates, addresses, and document IDs against 300+ trusted data sources through one API or directly via the ScreenlyyID platform.
- Flexible Solution
- Constant Updates
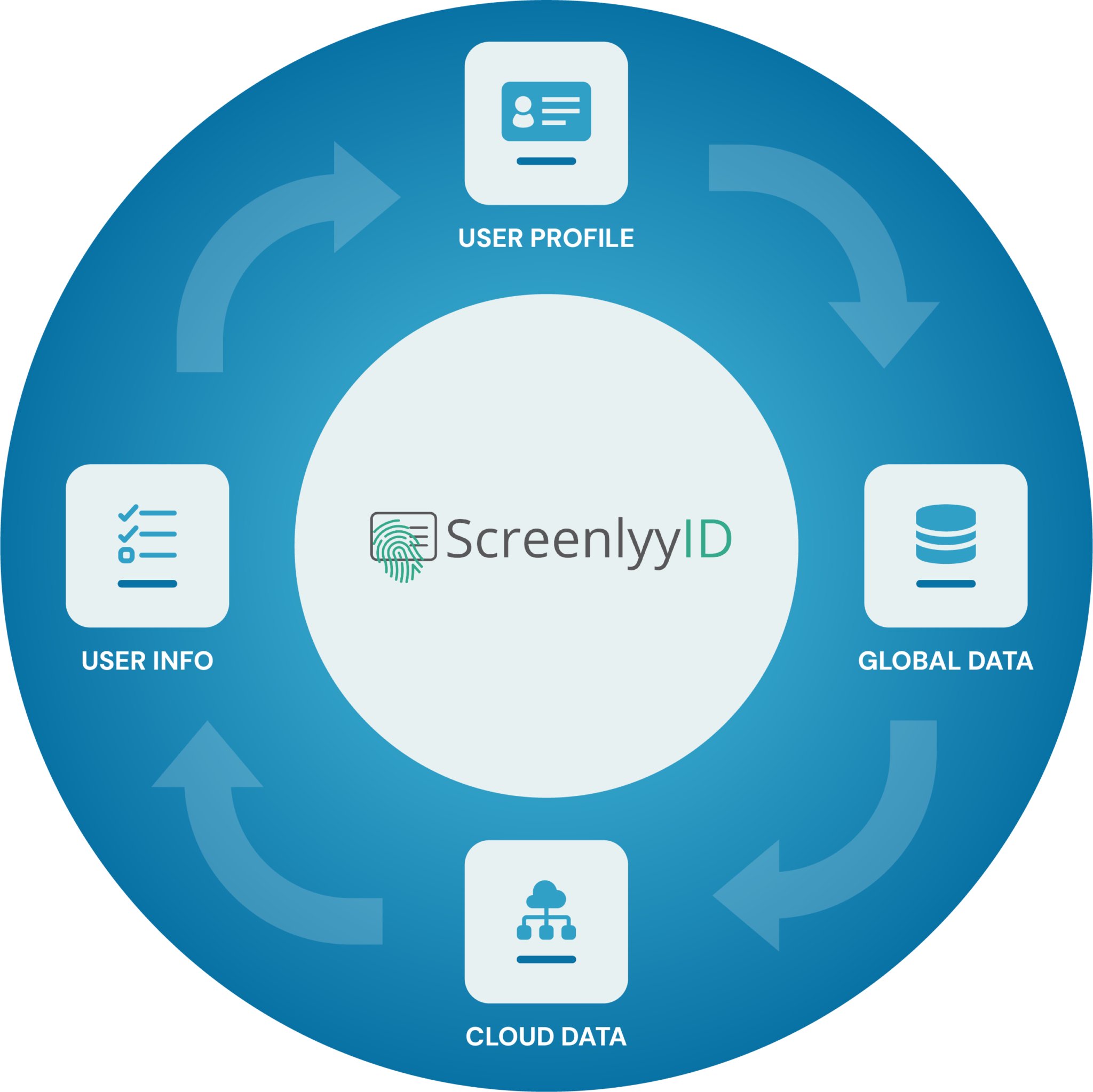
How Does eIDV Work
Effortless eIDV, no documents needed
Our zero-friction eIDV - electronic identity verification, process ensures swift customer onboarding without requiring paperwork or physical documents.
Extensive eIDV Data Sources
Data sources we use for eIDV - electronic identity verification checks
We utilize trusted data sources to perform accurate and secure eIDV - electronic identity verification, checks.
- Government
- Credit Bureau
- Telcom
- Utility
- Postal
- Consumer
- Commercial
Know Your Customer
Choose your security model
with 1 x 1 or 2 x 2 eIDV authentication
1 x 1 Single source authentication
eIDV 1x1, provides a matched result when the information provided is matched with one data source.
- Authenticates data against one data source
- Faster and more efficient response times
2 x 2 Dual source authentication
eIDV 2x2, provides a matched result when the information provided is matched with two data sources.
- Authenticates data against two data sources
- Meets stricter compliance regulations
How Does eIDV Work
eIDV, a truly global solution serving over 40 + different countries and growing
UAE
Argentina
Austria
Australia
Canada
Belgium
Brazil
Chile
Switzerland
China
Columbia
Czech Republic
Denmark
France
Czech Republic
Germany
Spain
Finland
United Kingdom
Ghana
Gibraltar
Greece
Hong Kong
Indonesia
Indonesia
Italy
Ireland
India
Japan
Kenya
Luxembourg
Mexico
Malaysia
Norway
Slovakia
Nigeria
Netherlands
New Zealand
Peru
Philipines
Poland
Portugal
Sweden
Singapore
Thailand
Turkey
USA
Vietnam
Romania
South Africa
End-to-End Fraud Management & Customer Verification
Combine eIDV with other ScreenlyyID solutions for full identity verification and anti-fraud protection.
Experience real-time analytics, seamless data integration, in-depth customer journey analysis, and powerful marketing tools.
Digital Identity Verification
effectively verify new customers in seconds, safeguarding your business from identity fraud
AML Screening
Use the extracted document data to run a full sanctions, PEP & global watchlist check on the individual.
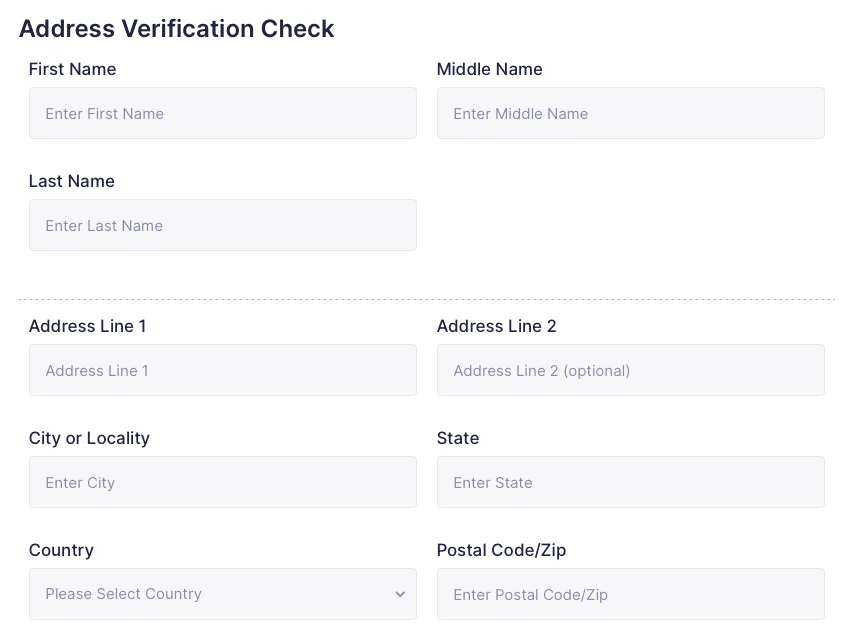
Address Validations
Validate and verify address’s in over 245 countries & territories. Simplify customer on-boarding, improve conversions.
Email Validation
Validate Email Addresses in real time Reduce fraud and verify real users.
Phone Validation
Define each stage of work to see what’s important and where things are getting stuck.
IP & Device Fingerprinting
Identify suspicious users by detecting harmful IP's, detect malware, attack sources, bots and botnets.
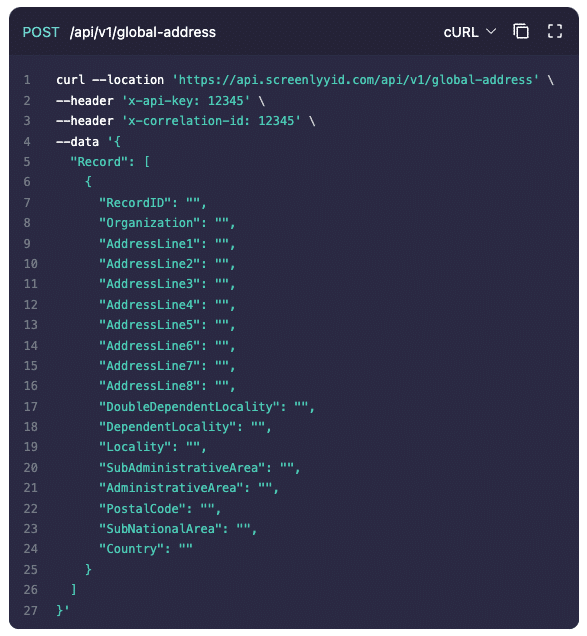
Simplified eIDV Process
No-Code, Bulk CSV, API, or live lookup, we’ve got you covered
ScreenlyyID's dashboard and API suite offers flexible eIDV integration options. You can conduct bulk verifications via CSV in the dashboard, integrate the API into your own systems, or send a no-code UI form to prospects for easy completion.
Frequently Asked Questions
We're here to answer all your questions
Everything you need to know about ScreenlyyID's eIDV - electronic identity verification solution. Can’t find the answer you’re looking for? Please chat to our friendly team.
eIDV verifies customer identity by cross-checking information against government and public data sources in real-time.
Yes, eIDV supports identity verification in over 40 countries and growing.
Contact Us
Talk to an expert
Let's connect to discuss the possibilities and find the perfect solution for your business needs.
Complete the form, and one of our experts will reach out to you. You'll discover how our solutions can tackle your specific challenges, optimize your operations, and drive your growth.
- Explore industry-specific use cases
- Identify the best solution for you
- Get enterprise pricing
- Book a demo
Lets Connect....
Start Today
Start Verifying Customers Today
See how easily ScreenlyyID integrates verification into your onboarding process.
- Free Forever
- No Set Up Fees
- No Licencing Fees
- No Hosting Fees